If we had to name a key and critical characteristic of human relationships, it would certainly be trust. And surely no introduction is needed regarding its importance and criticality. However, when the discussion comes to how it is built and maintained between people, the landscape begins to blur. In an “old-fashioned” neighborhood, someone who keeps their word over time and whose estimates are verified, is considered trustworthy and reputable. Nevertheless, in the case of a car theft, it is the police who will verify the incident and provide the car owner with the evidence needed to proceed with any process. Here the police function as a “trusted third party”.
As a “trusted party” technology has always existed. All kinds of contracts are “trust documents” and function as valid evidence. Every time we put a coin in a vending machine we trust that it will trigger the right spring, so that the appropriate product falls into the pickup exit. Essentially we indirectly trust the technician who built/programmed it, but this trust is mediated by the machine. Or when we use a taxi for a trip, even if there is a suspicion of lack of trust in the person driving, at the end of the ride we will agree with the taximeter.
We would say that people use some kind of “communication protocol” for their mutual and not only, understandings; and that these procedures are increasingly becoming the subject of mathematical logic. While therefore the “machine” is the specialist in mathematical calculations, it not only solves calculation problems. But it also offers itself as a solution to relationship issues, although it is of a technical nature. Or rather, faithful to the ideology of the times, because it is such. Objective.
We read the introduction of a text that presents a protocol with which “users” do not need to rely on mutual trust: 1
“Imagine the ideal protocol. It would include the most reliable intermediary – a solution that fits everyone. All parties would send their data to God. God would determine reliably and return the results. With God as the absolutely trustworthy confessor of our confessions, no party can know anything more about the data of other parties than what it can learn from its own data and the final results.
Unfortunately, however, in our ephemeral world we deal with people and not with deities. Nevertheless, very often we are forced to deal with people in an almost theological way, because the infrastructure (with which we communicate) lacks the required security that would protect us. […]”
The technology of a “chain of boxes”, based on a similar line of thinking, is presented as a revolutionary change in the way transactions will be conducted and comes to confirm the changes in the paradigm of trust relationships. Let us try to understand it, starting from a somewhat technical analysis.

a distributed ledger
The blockchain is essentially a new type of ledger. Ledgers are used to record the various transactions and movements that take place, as well as to store the history of these movements. In the past, there were paper ledgers, and with the advent of computers, this process was digitized. However, although ink on paper was replaced by bits on hard drives, the basic operational model remained the same: a database that is created, updated, verified, secured, and maintained in the same specific way.
For example, a bank has its own records with the information it needs: customer details, transactions and various other activities that occur, account statements, etc. Similarly, a hospital maintains a database with patients and their history or doctors and their related information. In a supermarket, accountants record various information about purchases and sales that take place, as well as payroll and taxes.
In the case that someone wants to check their account balance, they must make a request to the bank (e.g., inserting a card and PIN into an ATM), which will be verified for validity (card and PIN identification), and if everything goes well, it will be approved (the amount will be displayed on the screen).
To buy a house, the buyer will need to present proof of their financial status, while the owner must prove that they own the building. The former will request the relevant information from the bank’s or tax office’s database, and the latter will obtain the title deed from the notary.
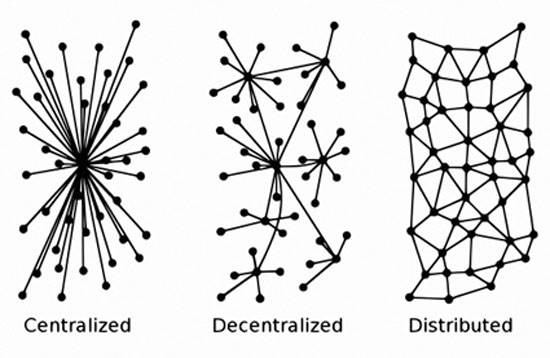
Examples like these show how these databases operate and the relationships around them. We would say that these records are centralized, in the sense that they are owned by the specific entities/organizations, and access to them is only possible through these entities.
The fact that not everyone can access anyone’s banking or medical history is not an element of “centralization” but of security. Likewise, the fact that the information is valid is a matter of the reliability of the respective organization. Various entities/organizations/companies guarantee the security and authenticity of the data, and thus their customers/citizens trust them for the relevant processes.
In the case of blockchain, this ledger/record is not stored centrally anywhere. It exists, is updated, and maintained on every node of a distributed network. Each node has a copy of the entire ledger: the states of the nodes, the history of transactions between them, etc. Security is a matter of cryptography, and the authenticity of information is ensured through various techniques and algorithms.
Considering that we know the classic way centralized databases operate, to understand the “distributed ledger,” we need to examine the components that make it up and how they respond differently to basic processes. What is a distributed network and how is it implemented? How are transactions conducted, and by what means is consensus achieved on their validity? How is security and privacy achieved in transactions? The first and most fundamental application of blockchain to date, Bitcoin, will help us explain some basics.
blockchain and cryptocurrencies
Because blockchain became widely known through bitcoin, there is a mistaken impression that these two are identical. In reality, blockchain is to bitcoin what the internal combustion engine is to cars: a technology that can have different applications. So, what are cryptocurrencies?
By the term cryptocurrency, we mean a virtual/digital currency used as a means of transaction via a network of computers (where a computer can now also be a “smart” refrigerator) and uses blockchain technology to ensure the validity of transactions. Currently, there are over 2000 different cryptocurrencies. 2 This happens because it costs nothing to create a cryptocurrency. However, its value 3 is created by its circulation, that is, by how many people use it.
Cryptocurrencies are stored in digital wallets. Inside them, there are digital funds in the form of unique keys/codes. Each wallet has its own unique address, and transactions are conducted like sending an email; that is, user A sends an X amount from the address of their wallet to the address of user B’s wallet. In this transfer, no central “trusted authority” intervenes to approve or reject it—what intervenes is the same as in an email transmission (the two computers, the internet, and the nodes between them), along with the blockchain technology process that undertakes the role of security and approval.
From a topological perspective, the bitcoin network relies on the physical infrastructure we know as the internet, but logically creates a distributed network among the computers of its users. Let’s assume that in such a network, information communication occurs by following a path between nodes rather than seeking a central one to provide the relevant information. For example, for user A to send a message to user B, the search for B’s address would be done by “asking” neighboring nodes and thus proceeding through the network until B is found. In a centralized network, user A would simply “ask” the central node that holds all addresses directly. 4
The computers participating in this network are called “nodes,” and apart from their digital wallets (in the case of cryptocurrencies), they store the entire ledger with the history of transactions that have been executed and approved on the network. Thus, they participate in the process of confirming subsequent transactions. The more nodes that participate, the greater the network’s security and the ability to verify the authenticity of data and transactions.
There is also the possibility for someone to be a simple user and not a node; that is, to have only their digital wallet on their computer. This way, they can make transactions but do not contribute to the broader operation of the blockchain. They simply assume that the network has as many nodes as needed to be secure and use it. This often happens because nodes must be permanently connected to the network—something that offers no reward beyond the moral satisfaction of making the network more secure. Many users do not want to dedicate a machine exclusively for this purpose.
Finally, there are also the miners, who play an important role in the transaction confirmation process.

digital excavators
These machines must have sufficient processing power, because they need to perform some difficult calculations. Each time they find an answer to such a calculation, they earn a quantity of bitcoin. So there is also a material incentive for someone to be a “miner,” beyond the ethical aspect that this makes the network more secure.
The bitcoin algorithm is designed in such a way that it increases the difficulty of calculations when it “sees” that these are being done faster than they should be. Initially, the idea was that anyone could play the role of miner with their simple computer, but competition among users has skyrocketed the difficulty of calculations.
The race for faster computation has increasingly raised the need for “powerful” machines and greater energy. After the computer and the complex constructions that use processors from many graphics cards, special mining machines were created, which now operate in huge “farms” where there are suitable temperatures and cheap electricity.
Ordinary users can no longer earn bitcoins from mining, unless they are willing to buy as many ASICs as they can (plus electricity costs), to participate in online collaborative mining operations organized by various entities (mining pools). Even then, however, the profit will be infinitesimally small. There is, of course, also the possibility of investing in mining a less well-known cryptocurrency, where the relevant calculations are still easy, in the hope that in the future this cryptocurrency will expand in use, and therefore in value.



the validation algorithm
What then is this verification process and how does blockchain technology, by claiming users’ trust, ensure the authenticity of information? How is consensus achieved on who has how much and which transactions are valid, in a distributed network where no specific person holds the ledger, but everyone has one, which must be synchronized with the others?
There are several “consensus algorithms” and the following is the one used by bitcoin. It is called “Proof of Work” and so far it is the most widespread, as it is considered one of the safest; while a major drawback is that it requires high energy consumption. 5
Let’s assume that user A (Alice) wants to send an amount to user B (Bob). Through her wallet application, she will make a transaction request to send amount X to B’s wallet. This request enters the network, into a “pool” of unconfirmed transactions.
At regular intervals, miners select some unconfirmed transactions from the pool and create a new block. 6 During this selection, a first comparison is made between the chosen transactions and their stored history, so as not to include invalid movements in the block. That is, if they see in the blockchain history that A’s account does not have enough bitcoins to send to B, they will reject the transaction.
Whichever miners have completed creating their block, begin the process of a difficult calculation that requires significant computational power, called “proof of work”. Whoever finds the answer to their problem, 7 sends it along with their block to all nodes.
They check whether the answer to the problem is indeed correct and finally confirm, based on their own stored history, the transactions included in the block. If everything goes well and the majority agrees, a new block can be added to the chain.


proof of work
The central step of the algorithm, therefore, apart from the comparison of the ledgers that each node holds, is this calculation that the “miners” perform; which uses “hash functions”.
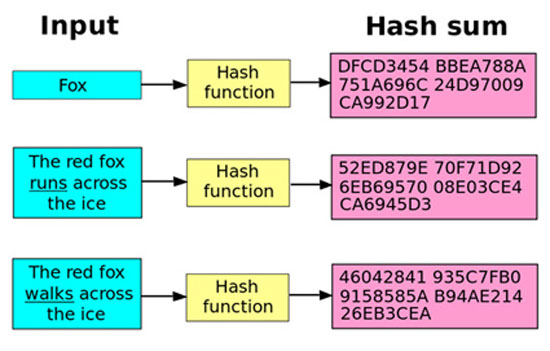
Hash functions accept an input of data of random size (anything that can be converted to bits: numbers, letters, images, sounds, etc.) and produce as output a fixed-size integer (hash value or key or sum). This number corresponds exclusively to the input that generated it. 8
The problem that the miner processes is to find a hash value of the block they want to add to the chain; which must start with a specific number of zeros. The number of zeros depends on the difficulty level set by the bitcoin algorithm, as we mentioned above.
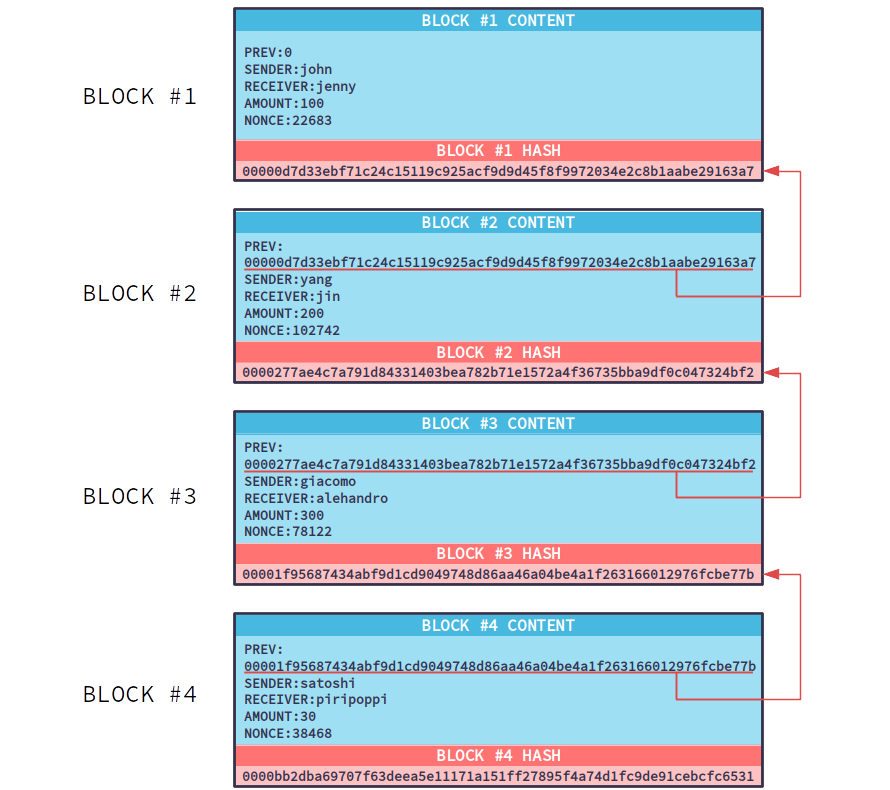
Let’s assume that a miner wants to calculate the hash value of the block they have created and the difficulty level at that moment is four zeros. The block contains the following:
1. The hash value of the last block (PREV).
2. The transactions that are to be confirmed (TRANSACTIONS).
3. An auxiliary number that we call NONCE.
All of these are entered into a hash function and produce a unique number as a result. If this number does not start with four zeros, the miner increases the nonce by one and re-enters the data into the hash function. This continues until the number nonce is found, which in combination with the specific data of the block, produces a hash value that starts with four zeros.
This process is time-consuming, but it is very easy for the remaining nodes to verify the answer. When their miner sends the block, which contains the correct nonce number, the remaining nodes simply need to pass it through the hash function once to see that the result indeed starts with four zeros.
The reason this difficult computation is performed is simply and only for the miner to prove that they worked. It does not contribute in any way to calculating a value that has some utility in the overall process. It is simply proof that the necessary energy and time were spent.
In this way, it is difficult for anyone to propose transactions for confirmation. Each node has agreed to the condition that it will accept blocks with transactions for confirmation only from someone who has spent the required energy.
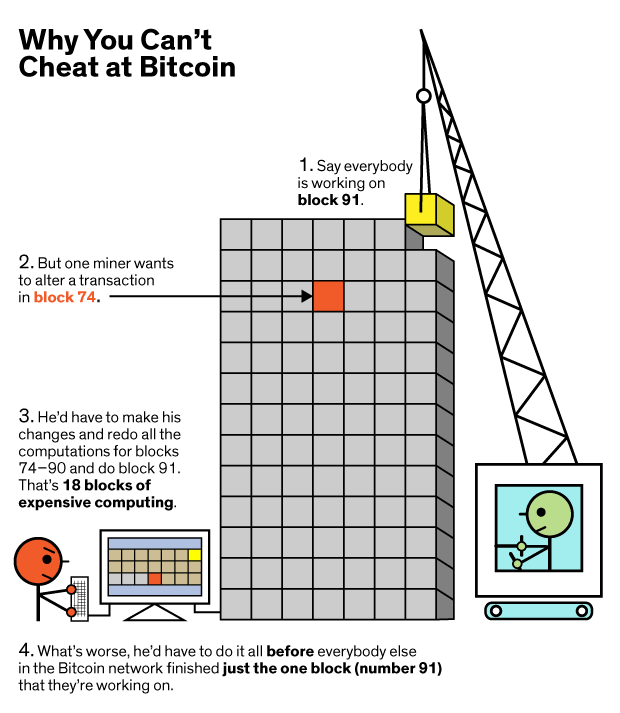
If anyone wishes to alter the data of a block, they must manage to re-calculate the hash value of that specific block (since the transaction data will have changed, the existing hash value will no longer match) – and all subsequent blocks up to the end of the chain (since each block connects to the next via the hash value). Alteration could theoretically occur only if “malicious” users acquire 51% (or more) of the network’s processing power, for as long as the calculations require. 9
temporary epilogue
Returning to the example of monetary transactions, the reason we trust and use banknotes is because there is an institution (the state, the central bank) that guarantees their value’s authenticity. And there is a “consensus” among citizens to accept these documents as reliable means of exchange.
With blockchain, the entity guaranteeing the authenticity of value is technology itself. And there is consensus among participants that in these specific transactions, the respective algorithm is what ensures their validity. And since the algorithm isn’t a group of idle clerks that can be bribed or fall “victim” to corruption, it is certainly more trustworthy for such tasks.
At first glance, the above may seem complicated—and in a way, it is. Perhaps, however, it helps to emphasize that essentially the only new element in all this is the process by which a miner “produces” trust. The process of calculating value through the hash function (proof of work).
New, not from a technological standpoint, because hash functions existed before. As did “distributed networks,” encryption, and even “consensus algorithms.” In essence, no technology is truly new; all existed beforehand. It is simply their combination, with the integration of the “proof of work” element, that makes blockchain “new.” And we could say that this is where the central “key point” lies.
The reason why each “miner” gains credibility—and consequently the entire blockchain endeavor—is the fact that they have spent considerable time and energy. That they “worked.” In a sense, they produced value. The value, we could say, that trust holds. But can machines produce value?
The discussion about the solutions blockchain offers and the ideology it embodies is vast, and certainly a text like this only touches the surface. Here, we tried to make a first approach to blockchain as a technology, through the example of Bitcoin. The real interest, however, lies in its application capabilities in other fields where values are exchanged and there is a need for a secure and valid data base. Some of the many examples include travel documents and services, electoral processes, and medical records.
In the process of exchanging money, the role of trust and the approved intermediary is somewhat clear; and since the concept of value is directly related to money, it’s no surprise that blockchain’s first application was digital currency. But when the concept of value expands to include relationships we cannot currently imagine, this role becomes increasingly blurred. Not so much in its form and presence, but in the process it follows. The proof that you cannot buy something because your account is empty is a mathematical process easily implemented by an algorithm. The process that proves, however, that you are guilty of something, goes beyond mathematics.
And more broadly, the idea of replacing the “machine” of bureaucracy literally with a machine, though old, unfolds before us, presenting new examples that should concern us. We will return to this.
Wintermute


