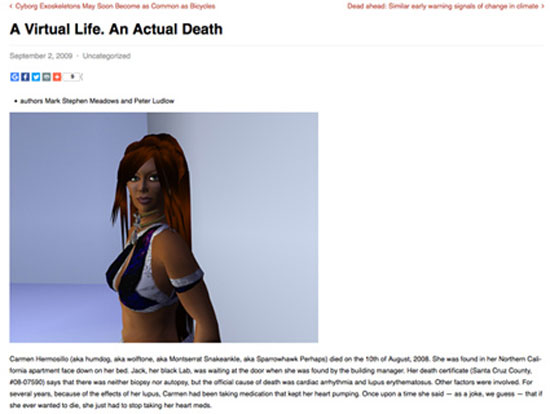
In our territories, these are completely indifferent matters; what are serious are the political buffooneries and the everyday trivialities. In other societies they have begun to understand the seriousness of …
blockchain: the protocol of the gods
If we had to name a key and critical characteristic of human relationships, it would certainly be trust. And surely no introduction is needed regarding its importance and criticality. However, …
Falling onto the tracks doesn’t stop the train
Washington is trying to brake the global expansion of Chinese-origin 5G communications technology, codenamed Huawei. Right now Huawei is far ahead of every competitor worldwide: not just in research but …
the archaeology of cyberspace: the cry of Pandora
The cyberspace did not leap fully armed from the head of the informatics Leviathan. It was constructed, developed, and infiltrated every field of human activity in a methodical and by …
Social responsibility
Who would disagree? If you have a pet and you don’t take care of it, you’re an unworthy “owner”. In distant e-China this is not idle talk. Every dog owner …
artificial intelligence: the Golem of the 4th industrial revolution
You might remember it, or maybe not. There is a method in statistics, quite simple and widespread, so much so that it is often taught even in high school. It …
Make a wish…
The Japanese “Astro Live Experiences” (ALE) wants to be the first to offer (for a fee) “artificial star showers” – the Perseids or shooting stars, which when they fall naturally …
singularity: technological fetishism and political economy in the 21st century
The concept of the “singularity” refers to the moment when technological evolution will result in producing an artificial super-intelligence, which will bring about unimaginable changes in human civilization. Some futurologists, …
Public order above all
At the beginning of last December, the Australian parliament passed a law requiring telecommunications companies to provide the security apparatus (police, intelligence services, etc.) with access to encrypted information; in …
- Page 2 of 2
- 1
- 2