Washington is trying to brake the global expansion of Chinese-origin 5G communications technology, codenamed Huawei. Right now Huawei is far ahead of every competitor worldwide: not just in research but …
Public order above all
At the beginning of last December, the Australian parliament passed a law requiring telecommunications companies to provide the security apparatus (police, intelligence services, etc.) with access to encrypted information; in …
Dragonfly
In Greek, this harmless (but impressive) insect is called a dragonfly. In English, it’s called a dragonfly. This name was given by Google engineers to a search engine (on Android) …
Deep fakes
If you have been alarmed (or angered) by how easily “fake news” spreads through social media networks, hold on to your seat. Technological advances in managing moving images, combined with …
Monitoring details
It’s not just “facial recognition” from a distance that captures the interest of law enforcement mechanisms (and perhaps others). With the title “Eyes in the sky: real-time surveillance system via …
Live tests
It is the largest open-air prison in the world, yet there is no reason for it to be left out of technological developments! The Gaza Strip—meaning its Palestinian captives—is a …
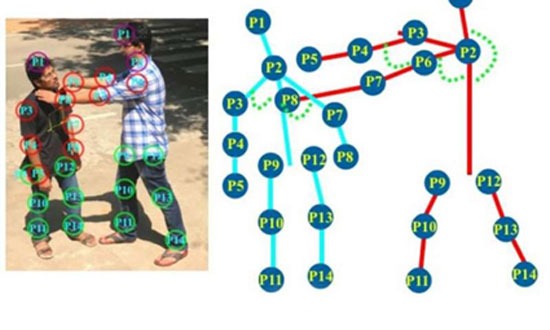
Eyes on the back!
It is called “intelligent classroom behavior management system”. And it is – strangely enough – an experimental application that was implemented in a Chinese high school. A camera with facial …
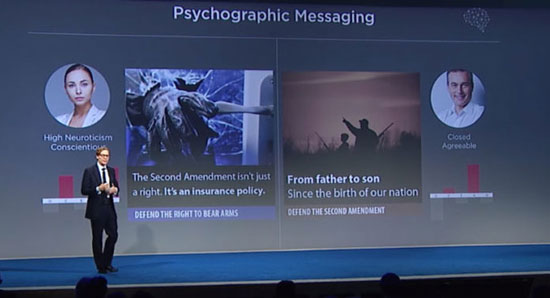
Cambridge Analytica: internal cyber psyops of the 4th world war
“Revelation! The Luftwaffe bombs London.” Such a front-page headline in a British newspaper, during the Second World War, would have certainly been unthinkable; war then was the directly experienced reality …
the second operating system that exists in every mobile phone device
Having discussed the issue of closed/open source code and without illusions regarding the technical solutions to the technological issues posed by the information age, we are publishing a translation of …
Drones
The flying machines of the big brother! For the police, they are the ideal complement to the generalized surveillance, but for a photographer they become the wedding videography tool and …
general data protection regulation: a digital habeas corpus?
much more than you think… “The goal of this new regulation is to give citizens back control over their personal data and to simplify the relevant regulatory environment for businesses. …
Αway from bad thoughts!
While some researchers are looking for what will, after all, eventually allow techno-science to help those taking exams to “remember all the material” (p. 56), others want to provide social …